Zone Transfer, which is often used in large organizations and is especially important for multiple DNS servers, can cause a serious security vulnerability if not configured correctly. Let’s take a quick look at what the DNS Zone Transfer vulnerability is and how to prevent it.
What is DNS?
The DNS (Domain Name System) is an advanced routing service that translates a human-typed web address into a machine-language IP address.
For example, an address like “google.com” makes no sense in machine language. If we tried to go directly to that address without a Domain Name Server, our host would have to look for the “google.com” server in localhost.
Domain name servers are critical because they store and route IP addresses and domain names. They provide efficient communication by distributing the load of traffic on the Web among different servers and regions.
What is a DNS Zone Transfer?
Zone Transfer, in network structures with more than one DNS server, is the synchronization performed by the main server, i.e. the primary DNS server, to keep the zone contents up to date. In larger network structures, there may be more than two DNS servers. These servers contain records such as Host, MX (Mail Exchanger), TXT, NS (Name Server), AAA (Address Record).
DNS zone transfer is the transfer of a DNS database to another server. This transfer can become a serious vulnerability, usually due to a misconfigured ruleset. It is a critical risk in enterprise environments, especially because it expands the attack surface.
Zone Transfer Test
The first test will show you how to block a zone transfer request on a properly configured server. There are a couple of different tools that can be used for this test.
- dig
- dnsrecon
- dnsenum
- host
Before testing, it is necessary to gather information about the target server, so the recon tools will be used. During the test, we will refer to all the tools, even though they perform the same function.
We have chosen Amazon as the target site for the test just for educational purposes. Amazon’s servers are correctly configured to prevent zone transfer. For this reason we should get “Zone Transfer Failed”.
1- Name Server Detection
The “dig” and “host” commands can be used for NS detection.
dig ns amazon.com +short
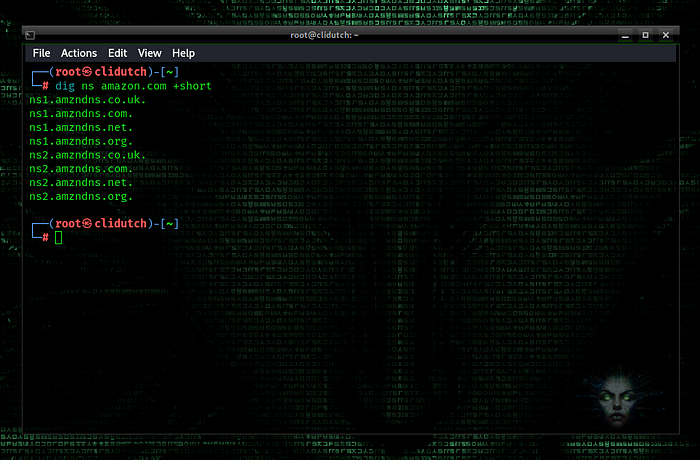
In this command, “ns” makes a name server query and “+short” makes a short query.
We have identified the target name server as “ns1.amzndns.com”.
The same result can be achieved with the host command.
host -t ns amazon.com
amazon.com name server ns1.amzndns.com
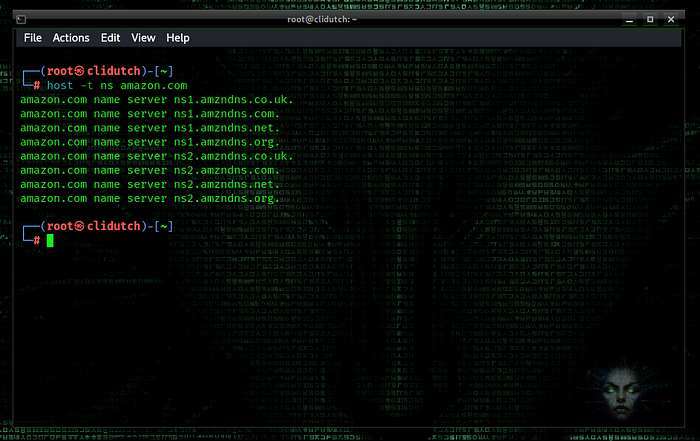
After detecting the target name server, the next step is the zone transfer test. It is possible to perform this test with 3 different tools.
- dnsenum
- host
- dig
2- Zone Transfer Test
First, I use the dnsenum tool.
dnsenum amazon.com
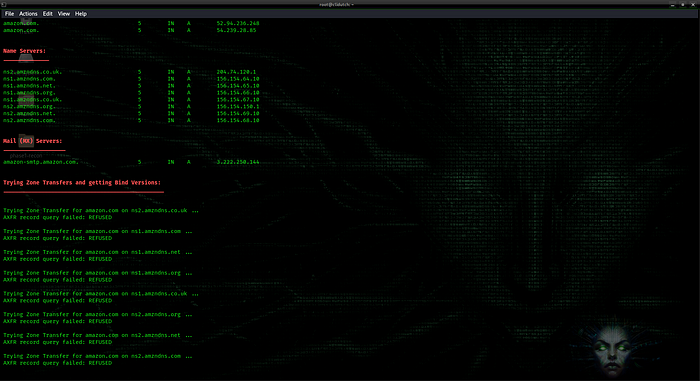
AXFR (zone transfer protocol) returns Denied. Zone transfer test failed.
It is also possible to perform the same test with using host.
host -l amazon.com ns1.amzndns.com
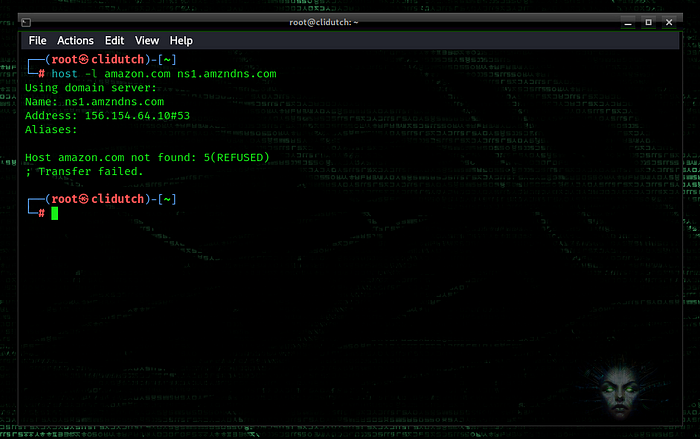
Make sure the main structure is [root domain][nameserver] when using host.
Now we try using “dig”.
dig @ns1.amzndns.com amazon.com axfr
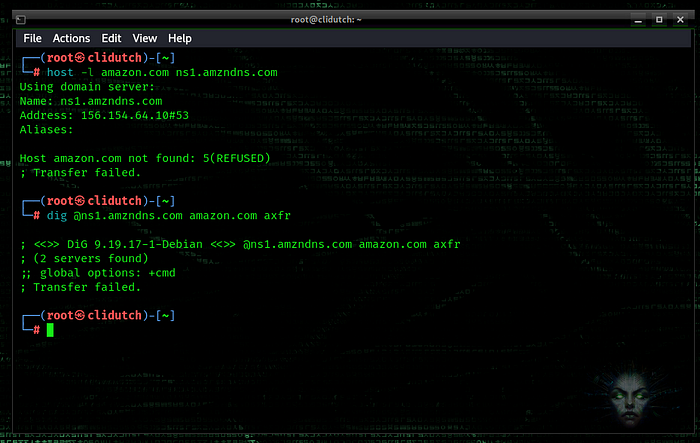
In the test with “dig” you have to select AXFR, i.e. zone transfer protocol. Otherwise dig will continue to return server info.
As a result, we could not perform zone transfer from a correctly configured server.
For the next test we will use “zonetransfer.me” because this address has a wrong ruleset specifically for zone transfer testing.
1- Name Server Detection
dig ns zonetransfer.me

host -t ns zonetransfer.me
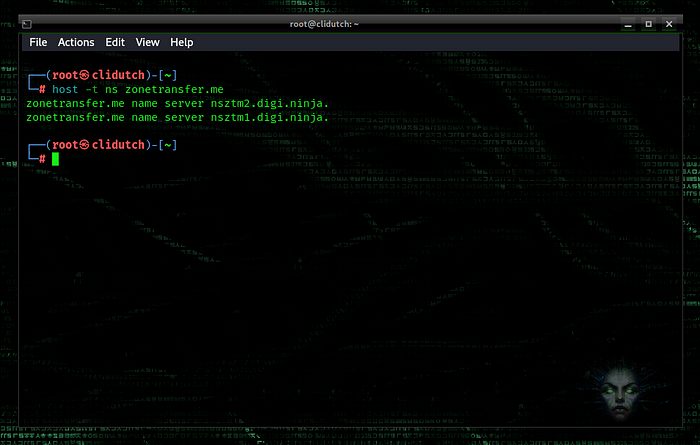
We’ve found the nameservers, now let’s test them.
2- Zone Transfer Test
dnsenum zonetransfer.me
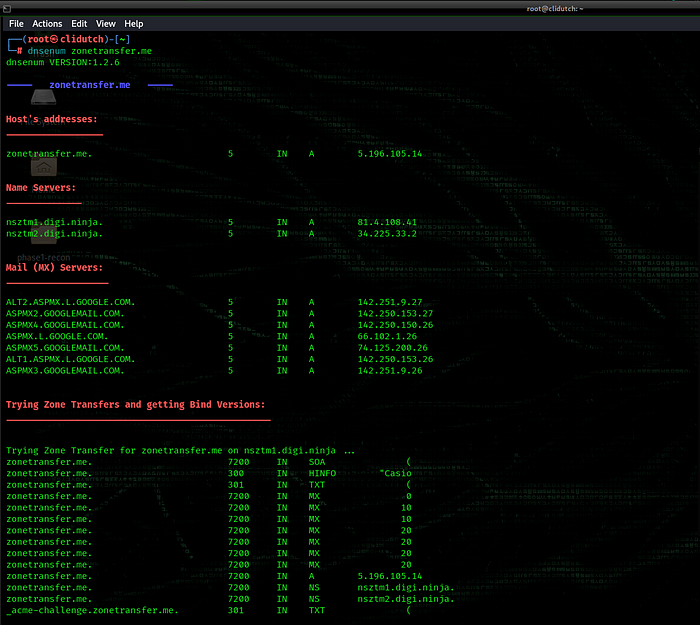
As we can see, the zone transfer test was successful, we transferred registers about NS, MX, TXT, AAA records are accessible.
host -l zonetransfer.me nsztm1.digi.ninja
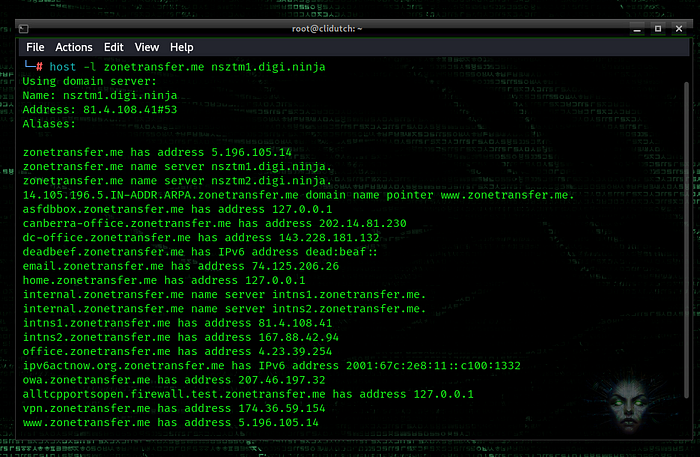
dig @nsztm1.digi.ninja zonetransfer.me axfr

Using the sample vulnerability in “zonetransfer.me”, we were able to transfer addresses from the corresponding server. In a real-world scenario, this will lead to critical vulnerabilities, especially in large enterprises, as it expands the attack surface.
How to Prevent DNS Zone Transfer Attack?
Firstly, DNS zone transfer is a critical operation required for DNS service. Although it can be exploited, it provides communication between at least two different DNS servers. Otherwise, if access to cached data is lost, all web, mail and other services under the domain will be inaccessible.
However, manually editing zones one by one increases the possibility of errors and takes a lot of time. For this reason, DNS zone transfer and record transfer are performed collectively. The simplest and most common protocol used for this transfer is the AXFR protocol. This request initiated by the client can cause the records to be leaked on a primary DNS server that is not configured correctly.
To prevent this, we can use;
[important]allow-transfer {“none”;};[/important]
should be used. However, if exceptions are to be made for different trusted name servers and IPs (for regular AXFR protocols), the BIND DNS exception can be recognized with an example like the following:
acl trusted-nameservers {
192.168.0.10; //ns2
192.168.1.20; //ns3
};
zone zonetransfer.me {
type master;
file “zones/zonetransfer.me”;
allow-transfer { trusted-nameservers; };
};
